Consensus¶
Deterministic Proof of Work¶
We implemented a new consensus protocol called Deterministic Proof of Work(DPoW) that guarantees the deterministic finality of transactions.
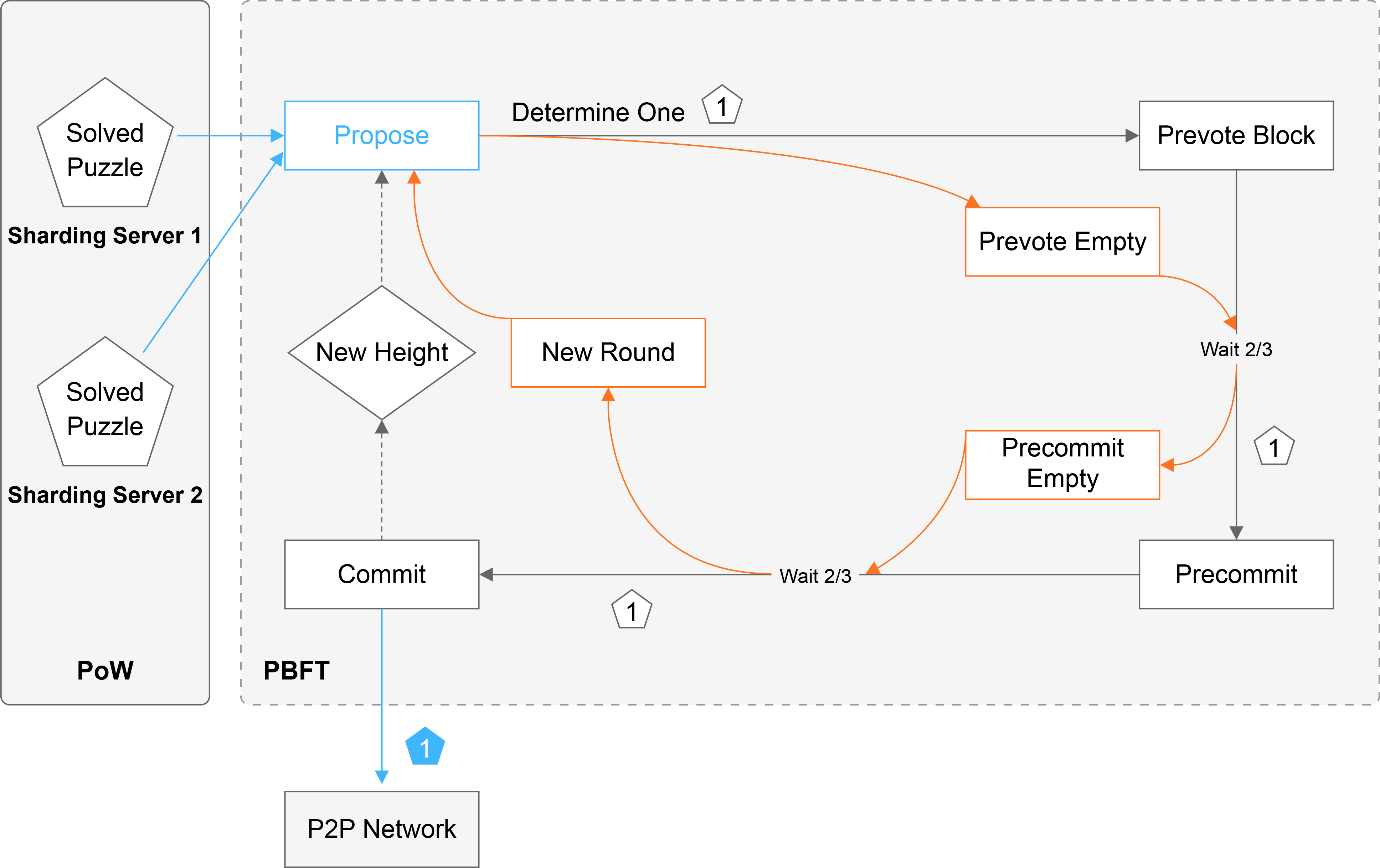
DPoW is a hybrid consensus protocol, it introduces a Map-reduce PoW mining mechanism to work alongside Byzantine Fault Tolerance(BFT) verification. It combines the advantages of both PoW and BFT, allows transactions to be confirmed immediately while keep highly decentralized. It assure strong consistency and security against a multitude of attacks largely because the protocol does not allow forking.
Verifiable Random Function(VRF) based verifier sortition mechanism¶
Of all consensus algorithms, BFT is particularly characterized by high consistency and efficiency. Nonetheless, at least 2/3 of all nodes in the system should be honest to ensure the safety and liveness of the system. Therefore, it is essential to select honest nodes as verifiers from so vast candidates.
Weighted Users
Reputation is very important in business. Our system quantifies the reputation of users and measures the weight of users by reputation. The verifier is selected by lottery, and the candidate with higher reputation has more chance of being selected. Under hypothesis that 2/3 of the network’s reputation is good, the chain’s security can be guaranteed. We believe that reputation-based weights are more fair than weighting method based on computing power or based on stocks.
Reputation : Reputation = F(Stake, Performance ,Nonce)
There are three factors for measuring reputation, stake, performance and nonce.
Verifier Sortition
The role of verifier sortition is to select candidates as block proposer or verifier whose identity can be verified by all other users.
The implementation of cryptographic sortition uses VRF: In the VRF algorithm, for a common input, the user can generate a hash value and a proof using its private key SK and a hash function. Other users can use this hash value and the proof, combined with the user’s public key PK, to verify whether the hash value is generated by the user for that input. The hash value determines who would be selected.
In the process, the user’s private key is not leaked at all from beginning to end. The user is authenticated in this way, and other users can believe his role as a verifier for a certain period of time. In this way, a set of users can be randomly selected through a common input and their identity can be verified by others.
Procedure Sortition(Stake, Performance,Nonce, Seed)
------------------------------------------------------------------------
reputation = Reputation(Stake, Performance,Nonce)
<hash, proof> = VRF(PrivateKey,Seed)
priority = Priority(hash,reputation)
return (priority, proof)
The purpose of our introduction of reputation is to make high-credit users more likely to be selected. Whether a certain user can be selected is not a deterministic event. The randomness in the sortition algorithm comes from a publicly known random seed.
Seed
Dipperin produce a public known seed for each height. This seed cannot be controlled by attackers or be predicted in advance; otherwise, an adversary may be able to choose a seed that favors selection of corrupted users.
The seed is produced by miners when pack new blocks. Once the network reaches agreement on the block for height r-1, miners can computer the next seed as Seed_r, proof := VRF(SK_r-1 proposer , Seed_r-1). Each random output of the VRF is unpredictable by any miner until it becomes available to everyone. The winner block of height r would determines the seedr.
Dipperin verifier committee members are replaced each 220 blocks. We call each 220 blocks a “slot”. The seed in the last block of Slot d (e.g. #299 block of Slot 3), determints the verifier committee members of Slot d + 2 (e.g. Slot 5).